I received two classic Becker car radios, namely the Becker Europa 2000 BE 1100. Unfortunately, the security code for one of them had been forgotten. Not wanting to pay for reflashing the radio in shady service shops, I investigated and managed to extract the code myself. In case I encounter another similar radio in the future, I will update this post.
Becker Europa 2000 BE 1100
And probably other Becker radios with four-digit code.
Dumping the EEPROM content
The code is stored in I²C EEPROM 85C82. This chip is compatible with 24C02 and has a capacity of 256 bytes. It is located on the upper PCB near the front side of the radio. Simply take off the upper cover; no unscrewing anything is necessary.


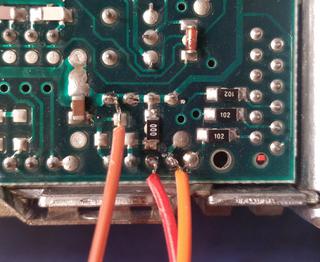
I soldered three wires to the chip and used Bus Pirate to dump its contents. In fact, any other EEPROM reader will do. To read it, issue two I²C commands: set the address pointer to 0x0, then read 256 bytes:
[ 0xA0 0 ]
[ 0xA1 r:256 ]
Bus Pirate prints a textual representation to the serial output. To convert it to a binary file, I’ve written the following Python script:
#!/usr/bin/env python3
import sys
if len(sys.argv) < 2:
print("usage: %s {text file dump from bus pirate}" % sys.argv[0], file=sys.stderr)
sys.exit(1)
def remove_prefix(text, prefix):
return text[text.startswith(prefix) and len(prefix):]
with open(sys.argv[1], "r") as f:
content = f.read()
values = [remove_prefix(v.strip(), "0x") for v in content.split("ACK") if len(v.strip()) > 0]
values = "".join(values)
values = bytearray.fromhex(values)
print("Dump has %d bytes." % len(values))
with open(sys.argv[1] + ".bin", "wb") as f:
f.write(values)
Calculating the code
The screenshot down below shows one of binary files I’ve dumped. The eye-catching ASCII-encoded number at the offset 0x71 is the radio’s serial number, which should match the one printed on the outer case (without the leading 1).

Examining my EEPROM dumps and other dumps found on the Internet with security codes attached, I determined that the security code is stored in two bytes, repeated three times, at offsets 0x5A, 0x5C, and 0x5E, respectively. Each digit is stored in convoluted BCD format. For example, the value C9 38 is radio code 6392, and A3 BA is 0910. By comparing some dumps, I discovered the encoding table:
| Screen digit | Hex value |
|---|---|
| 0 | A |
| 1 | B |
| 2 | 8 |
| 3 | 9 |
| 4 | E |
| 5 | F |
| 6 | C |
| 7 | D |
| 8 | 2 |
| 9 | 3 |
For reference, I provide two EEPROM dumps from my own radios: with code 3178, with code 0910.